Home / About the installation, databases and the environment
Related topics
▸ Types of databases and where you can stay
▸ Access to the database engine when hired Cloud or Hosting
▸ Uses the database of examples to practice and learn the system
▸ Basic concepts about the creation of new databases
▸ What is an access to the database?
▸ Selection of the Database when you enter the application
▸ How do I create a new database?
▸ Streamlined for the creation of databases on your local computer
▸ Advanced option for the creation of databases in the cloud or on a network
▸ Introduction to data migration from previous versions
▸ How do I migrate the information from my previous versions?
▸ Migration of databases without warranty
▸ Connection of the programs installed on your computer with the database
▸ Create a shortcut in your pc to connect to a database
▸ Connection of the database with mobile devices
The reason for registering the users who will have access to each database
Once you have created a database, it is important to define the users who will have access to it.
The reason why you must define the users due to issues of security, control and tracking.
- Security to allow access to the database only to persons or authorised users. To access the database, the program will ask you for a user name and a password that you define, allowing you to authenticate the identity of users accessing the database. This feature prevents unauthorized individuals from making changes to your information.
- Control since you have to define the action or operation permits the users will have authorized access to the database. For example:
– Users with full access
– Technical users
– Users only query
– Users with custom permissions - Tracking of actions. When you access the database on a shared basis in a network, all the actions that different users or persons authorized to perform on the database are recorded in the log of transactions, allowing you to follow up with a date and time to the actions performed by each user.
The amount of user names or authorized individuals who register to access each database is limitless. Therefore, the registration of users is independent and has nothing to do with the licensing scheme that you've already purchased that several different users could access the system sharing the same computer without having to purchase an additional license for each one of them.
Additional users have full access to that do require licensing to use the programs, they will be able to access the system unlimited users with profile of technicians and only query. These latter do not require licensing, but you will need to give permission for access, giving them high as a user in the database.
As the user registry is database, a user can be registered in multiple databases and in each have a different user profile.
What happens if I do not log users?
You'll be able to enter any of the programs of the suite, and access the database without having to registered users, such as a generic user, but this can have some drawbacks.
For example, if you don't register the users of the database, any unauthorized person could run the program and add, view or modify records in your database without authorization. Or, if you have computers with the system installed in your network and access the same database with the generic user, the first person to run the program will lock the database while avoiding other people to operate the program and to access the database on a shared basis. Here the importance of registering users, so that several users can work with the database at the same time and from different computers.
Then, it is necessary for the registration of users to allow the entry at the same time to a database.
When you access any of the programs of the suite, in the lower part of the system indicates the name of the user that you entered.
User manager databases
To be able to create users it is necessary to appoint a person as administrator user. This admin user will have the authority to enlist other users and set permissions or access profiles of every one of them.
Registering users and access levels
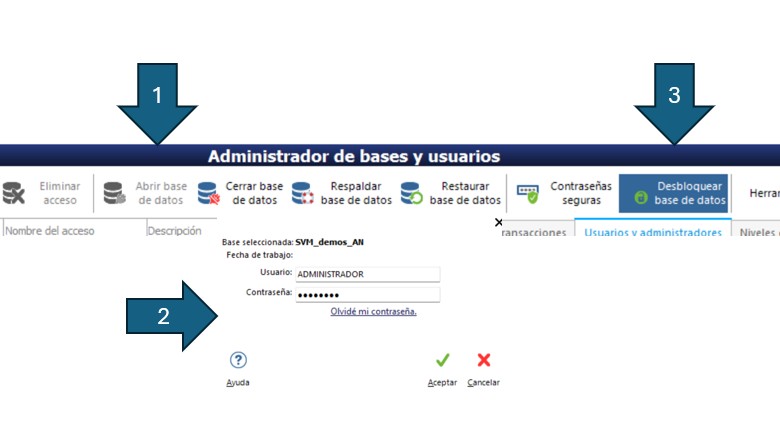
La creación y administración de los usuarios para las bases de datos se lleva a cabo con la aplicación “SVISION MANAGEMENT / Manager Databases and Users” located in the Windows start menu.
You can also run the application “SVISION MANAGEMENT / Administrador de Bases y Usuarios” from the selector application located in the programs of the suite.
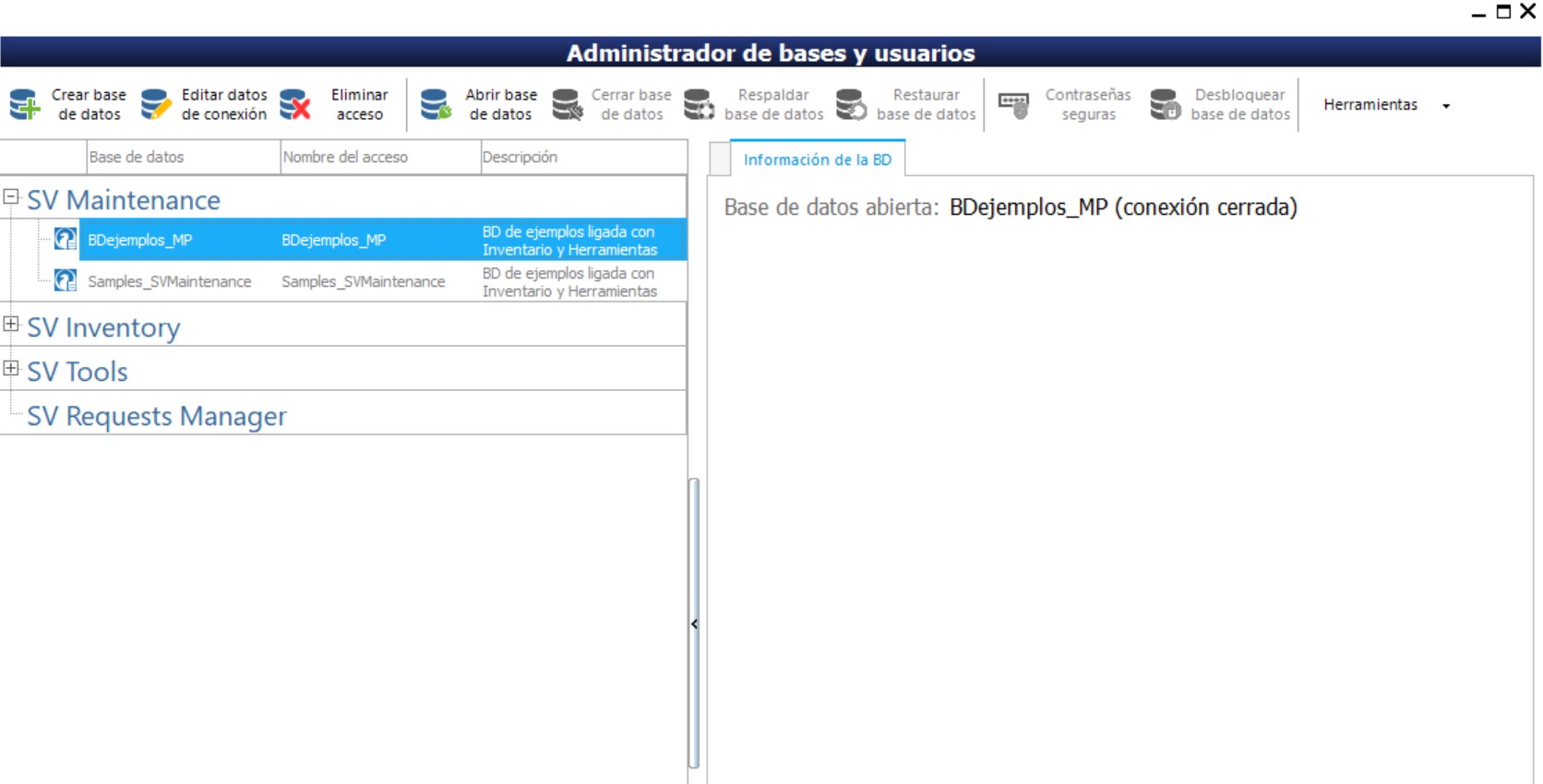
When you run the application “Manager Databases and Users” displays the list of pre-created databases that will be managed by the user administrator. If you have not created a database yet, you'll first need to create it. See creating databases.
It is also necessary that the user administrator set previously connection with the database who is going to manage.
If the list of databases appears to be empty when you run the application “Manager Databases and Users”, then you probably have not established the connection with the(s) base(s) of data and for the same reason, the program does not recognize the database created in your network.
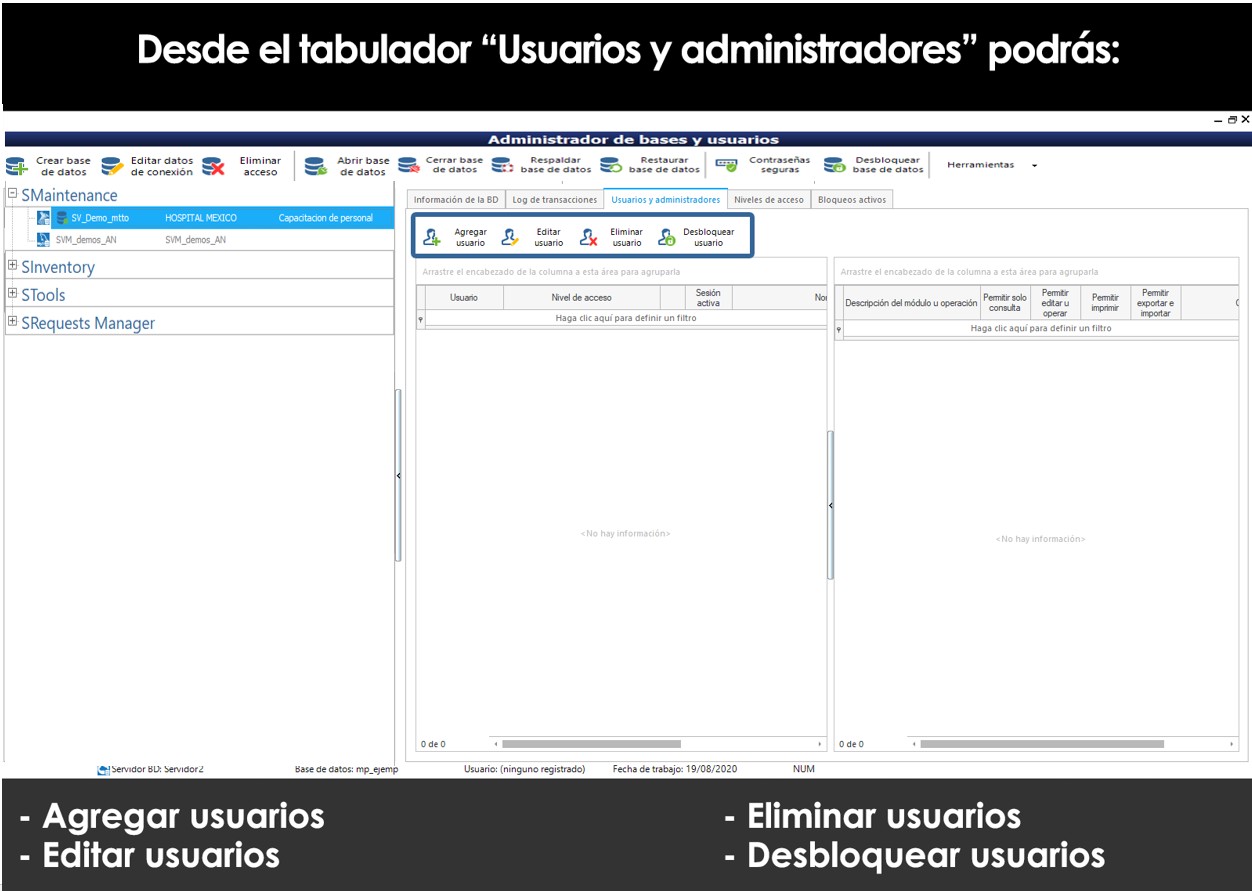
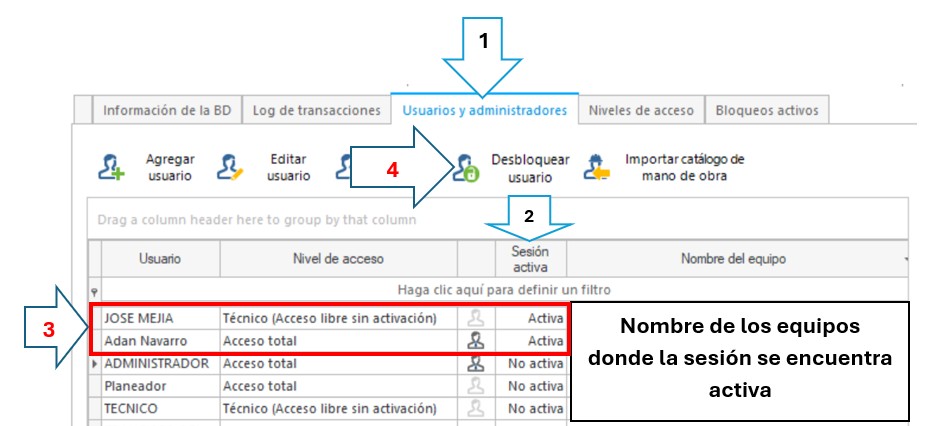
Add, Edit, or Delete users
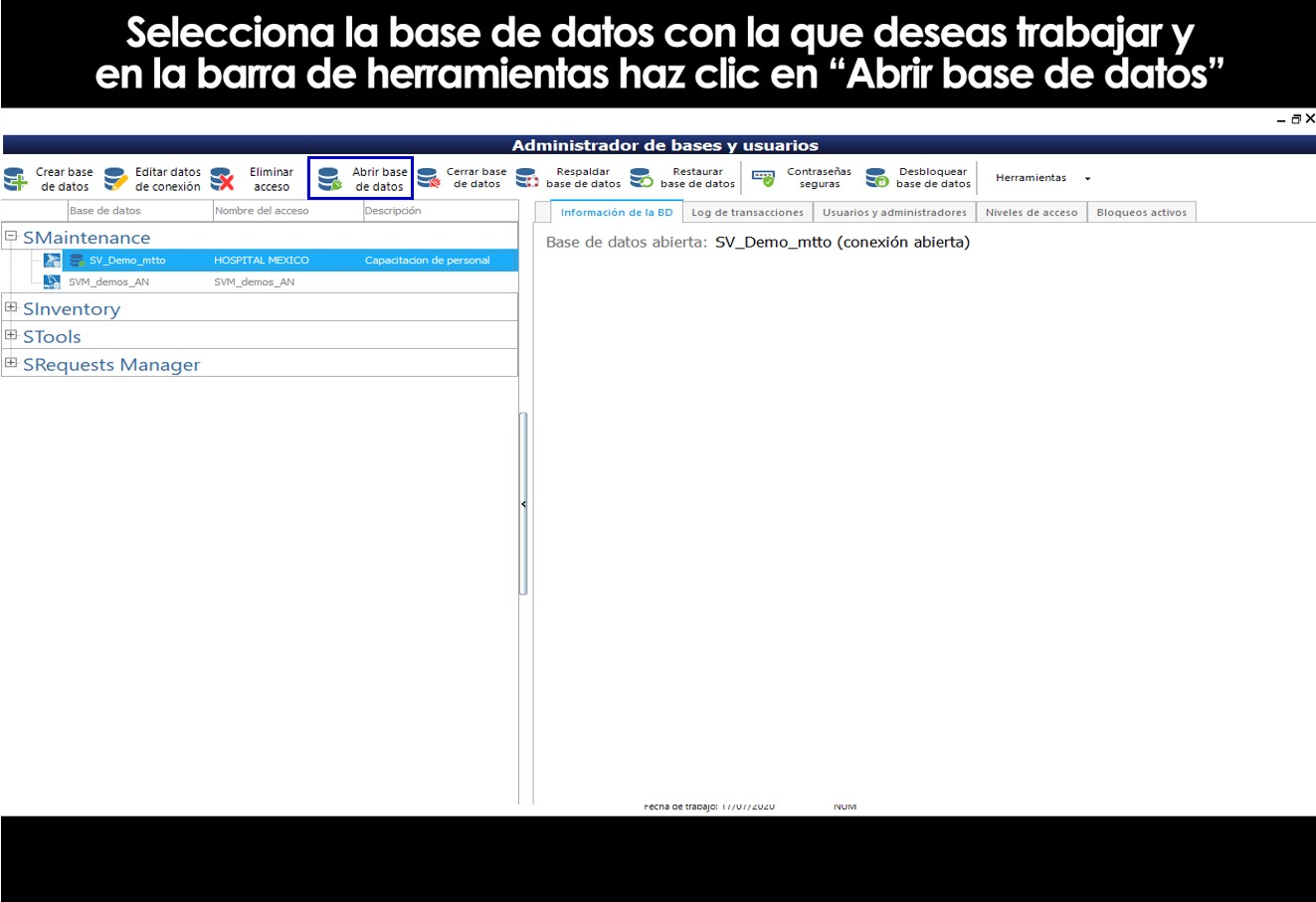
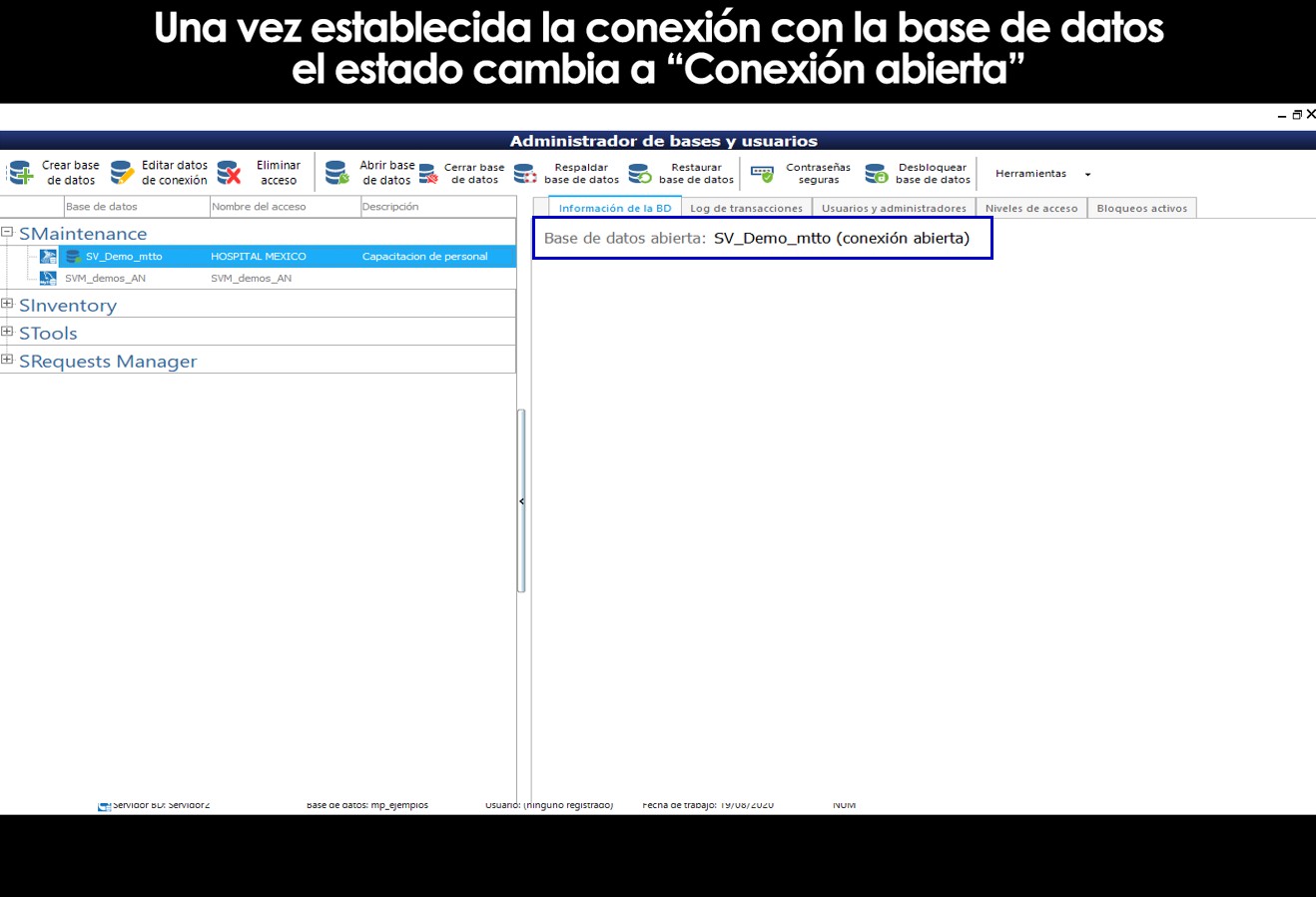
Once the connection of the user's computer manager with the databases, select the database to which you want to register users or permissions for users, click on “Open database” in the toolbar and in the tab “Users and administrators” you can Add, Edit, or Delete users to the selected base.
El primer usuario que agregues forzosamente debe ser el usuario administrador, ya que solo el usuario con este perfil de administrador tendrá permiso para crear usuarios adicionales.
When you add users to the user manager optionally, you can grant other users privileges of an administrator, but it must always be at least one administrator user in each database.
While you have not registered users, the system will be open so that any person can enter as a non-registered user. In the bottom bar of the system you'll be able to appreciate the legend that tells you when you do not yet have a user registered in the database.
Once you register the first user administrator, no person who is not registered in the database by the administrator user will be able to access the database. To do this, the system will ask every time you access, you provide your user name and password.
User profiles or levels of access.
The level of access it refers to the operation permits the users will have authorized access to the database. With them, you define whether a user will have full access or if you will be limited to certain modules and certain functions that may run.
For example:
– Users with full access (default)
– Technical users (default)
– Users only query (default)
– Users with custom permissions
The first three levels are factory preset and there is a fourth level of access that is configurable by the user administrator.
User Full Access
Paid License
The type of user with full access is appropriate for Managers of maintenance or for the managers of the store of spare parts, or tools.
This type of user is required to load all the information required for the implementation of the system.
Edit catalogs of equipment, locations, maintenance plans, stores and spares, etc
Plan maintenance activities
Manage and operate the inventory of spare parts, movements of inputs and outputs, calculation of supply, etc
Generate and manage work orders
Generate reports and graphs with the data analysis tools
Give high new users and grant permissions to existing users
Etc.
User Query
Free and Unlimited
This user type is suitable for people who come into the system only to make inquiries.
Consult all the information about teams and locations
Refer to maintenance plans
Consult calendars maintenance
Consult wos
Consult alerts
Check history
Consult consumption and spare parts assigned to each computer
Consult warranties
Consult suppliers and services
Check availability of tools
Refer to maintenance plans next
Consult a stock of replacement parts
Technical User
Free and Unlimited
The technical user is suitable for technicians who are running and build on each other maintenance work.
This type of user is also suitable for technicians who take readings and measurements of the equipment.
Perform all the functions of the user query.
Mark the activities of the wos
Record readings of the equipment (Eg. Mileage, hours of use, etc).
Record measurements (Eg. Temperature, amperage, wear, etc).
Generate vouchers store
Record consumption of spare parts used
Add comments in the wos
Mark teams that are out of service
Record time dedicated to the execution of each OT
Add pictures of how it was in the team before and after the work
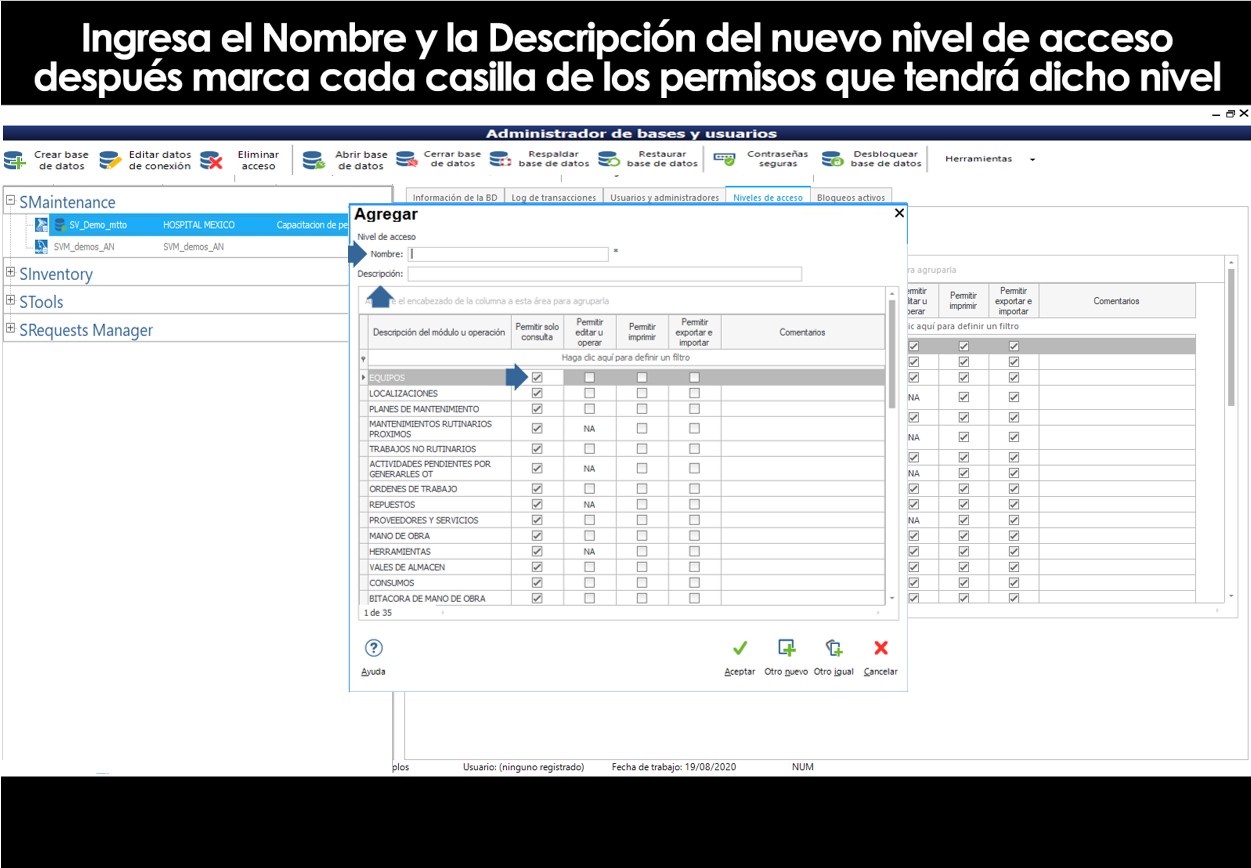
Al crear un nuevo usuario, podrás personalizarlo, o crearlo con los perfiles predeterminados
| Requirements to register a user | ||
|---|---|---|
| Field | Description | Length of the description |
| User | Name of person or job, example: John Doe, workshop Manager, Auditor, Manager of the department, etc | 50 Characters |
| Access level | Full access, technical, read-only, Custom. | Predefined |
| Password | Combination of letters and numbers | 10 Characters |
| Administrator of the database | Attribute that will be awarded to the exclusive use of the dba and users | Does not apply |
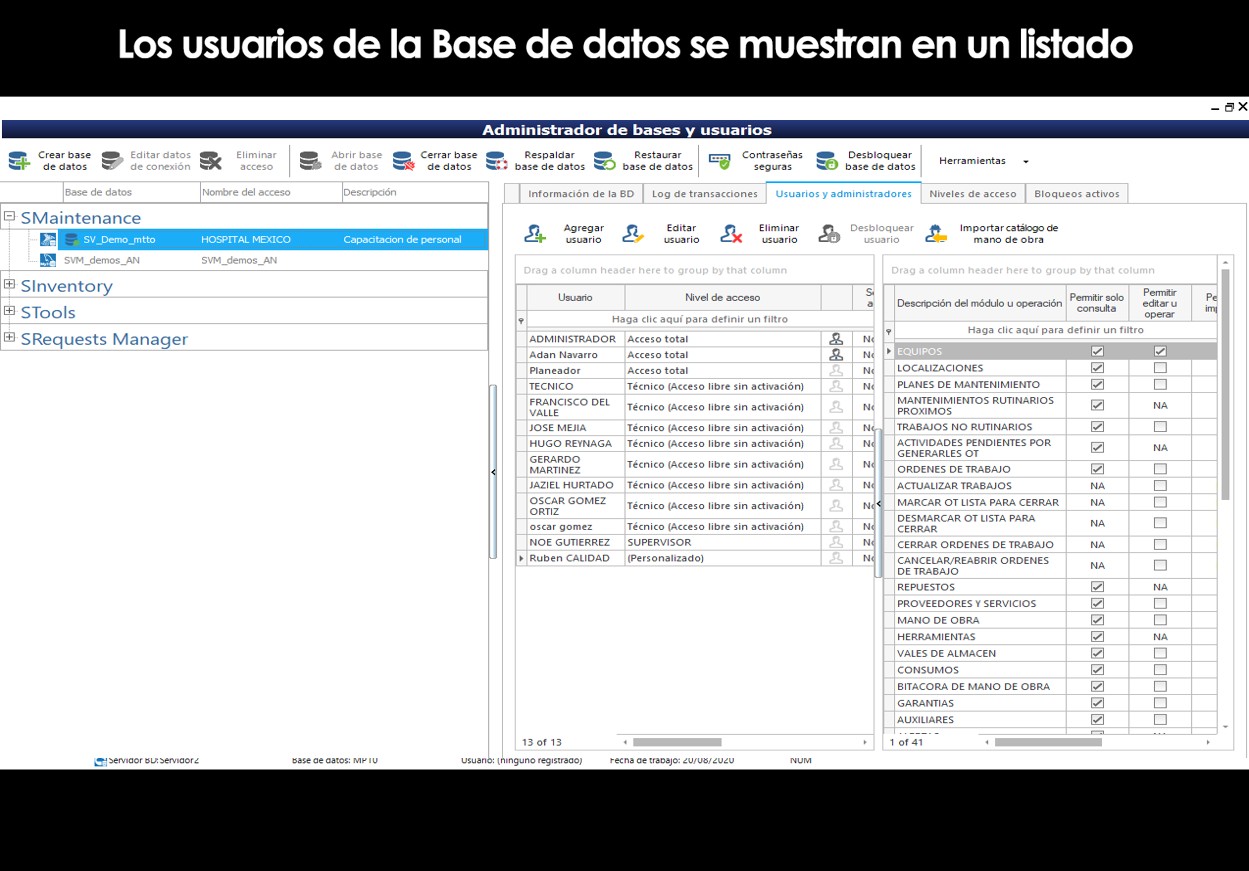
En la imagen se observa que se agregó a la lista de usuarios de la base de datos CON DIFERENTES Niveles de Acceso Total. Además, se aprecia una figura de un usuario resaltada que nos indica que es Administrador. Con otros usuarios que no son administradores, la imagen no se verá resaltada.
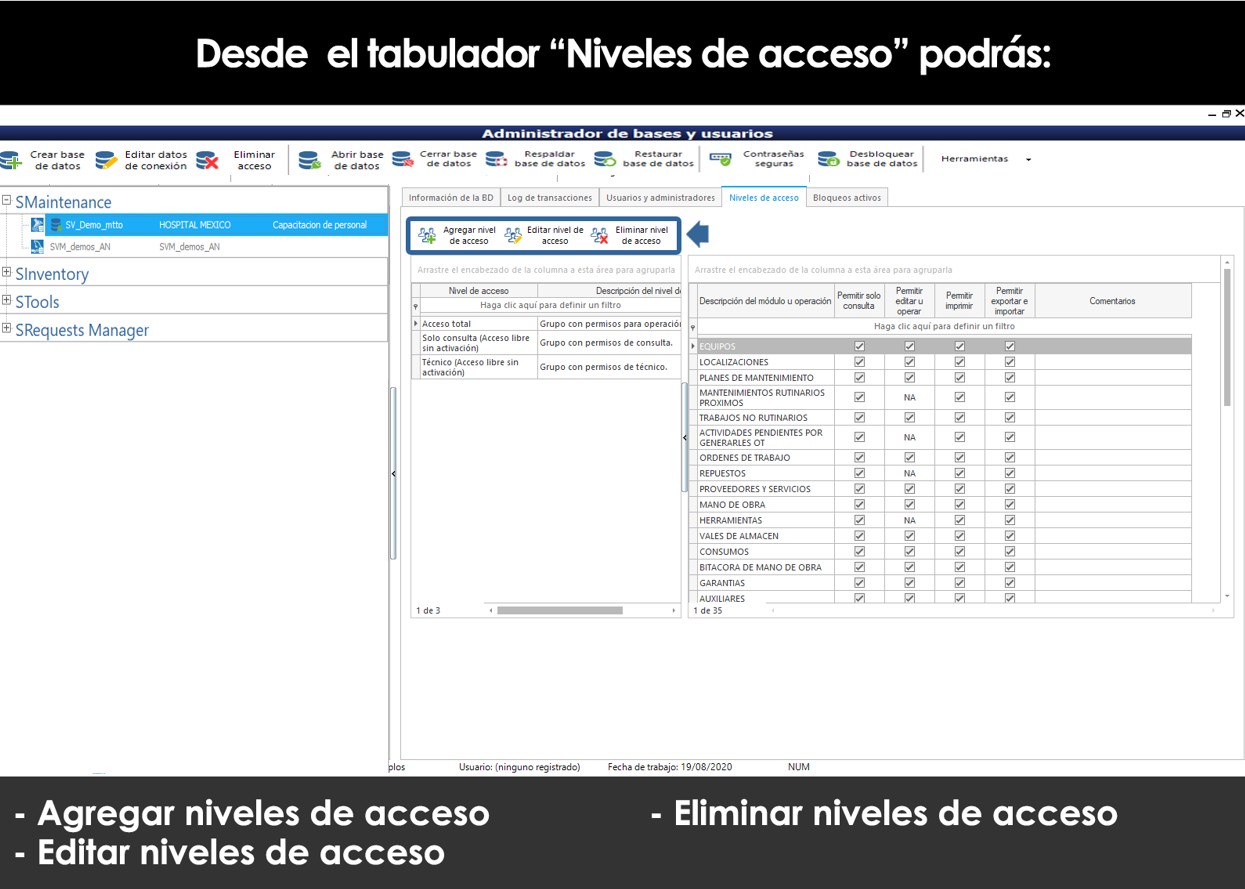
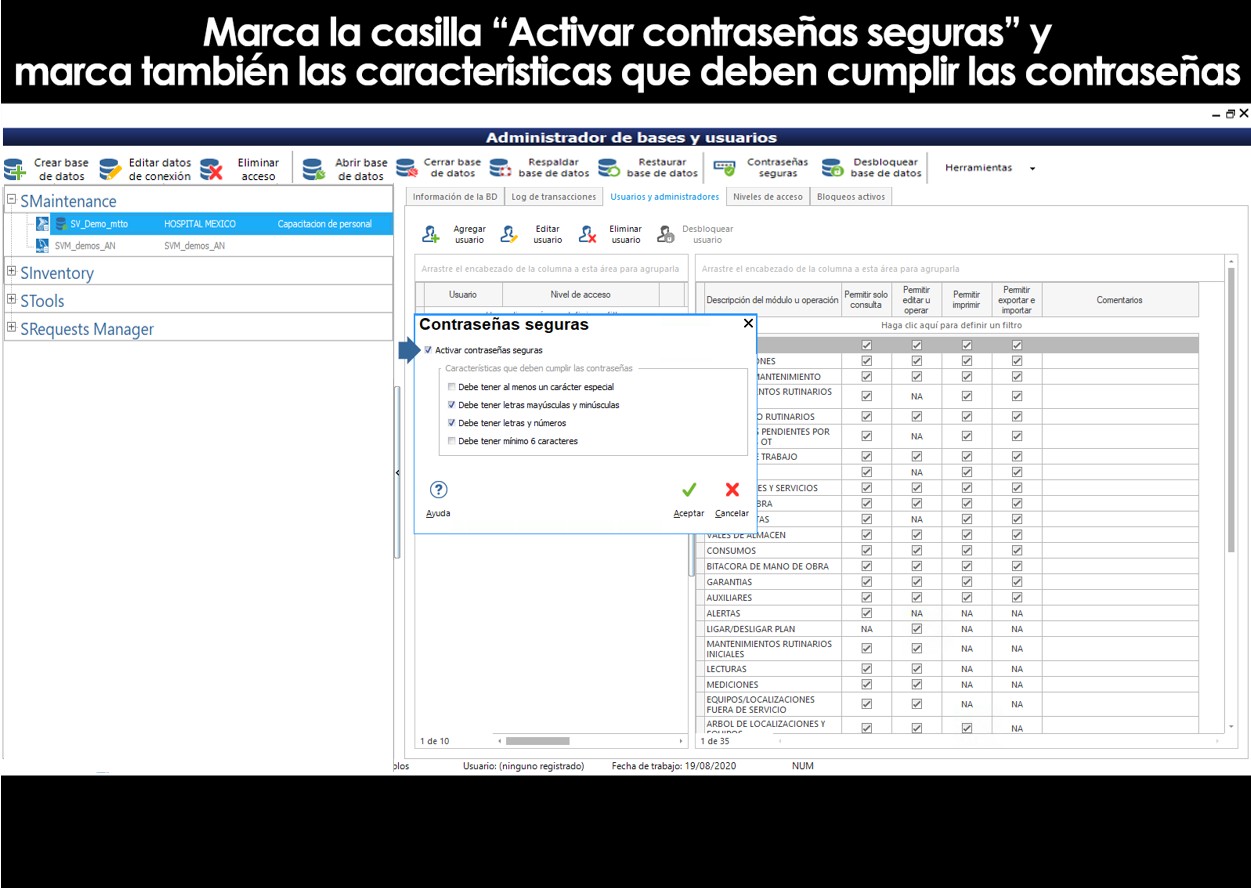
Create custom access levels.
SVISION te permite crear niveles de acceso personalizados, definiendo los permisos y funciones en forma personalizada.
To do this, click on the Levels tab, Access, type in a name or description to identify the level of access that you're about to create, and enables or disables the boxes defining the permissions and roles in a personalized way.
It is worth mentioning that you can only assign custom access levels to personnel or users who have installed the system with the License you Purchased, therefore, the Levels of Technical User and only Query that are free and unlimited may not be modified. It is not possible to change the permissions of a user or a technical Query only. All users that are custom must use a license on the computer that will be allocated for its operation.
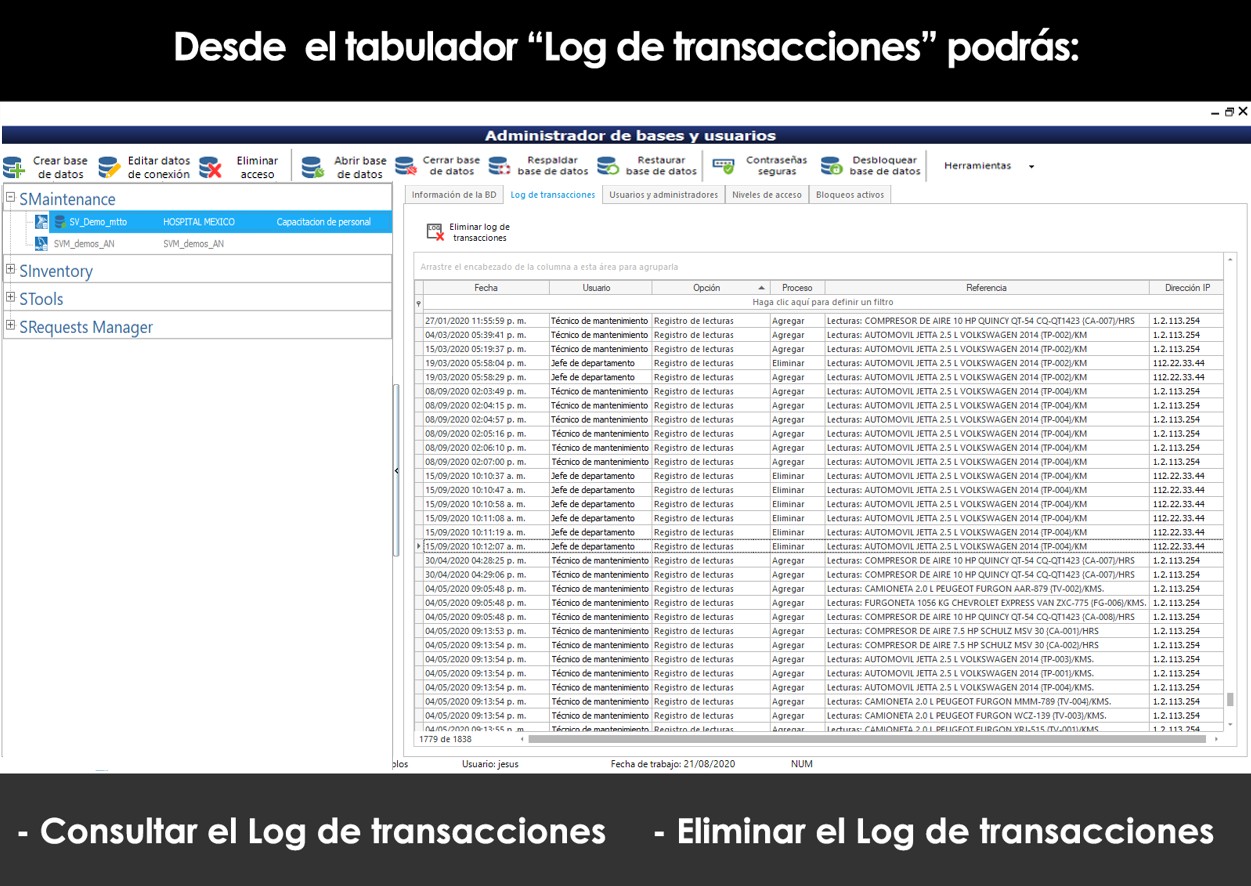
Log of transactions
The log of transactions is a function that allows you to check the activities carried out by the users so that you can view the log of operations performed per date and time. So you can know when and who performed some operation with the program. To access this option, you must select the database, open the database and click on the tab “Log of transactions.”
Shows the date and time in which it was a transaction, the name of the user, the function or option executed, the process carried out, the reference indicating, for example, the page in the document, the name of the computer and the network address of the computer where the transaction was made.
You can sort, filter, and group the information in accordance with a specific search you wish to perform
For more information, see sort, filter and group meshes of information.
Why arrives to hang a user and how to unlock?
When a user enters the database, it is recorded in the database as an active user. When the user exits the application and discontinue use of the database, it is marked in the database as an inactive user.
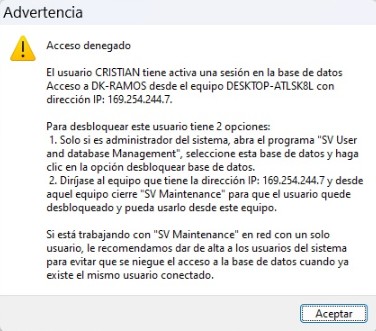
If for any abnormal situation the user quits the application and disconnect it from the network without properly closing the application, the user is maintained as active in the database and the next time when you try to run again the program, will be denied access because he was an active user, receive the following message:
Example of cases in which a user can be blocked for your re-entry to the application:
– Disconnect from the network by a court of light.
– Turn off or disconnect the power plug from the computer
– Close the application with the task Manager of Windows
– Unexpected restart of the computer caused by some update Windows
– Etc.
To perform the unlocking of the user is required to enter the app Manager Databases and users and unlock it.
Bloqueo 2
The unlock is per user, so that the other users will be able to continue working without any interruption.
A better reference is to enter the option Locks assetsin order to identify and select the User that by the time it is Active, click on Remove locks the user and computer selected, it will enable again the income to the blocked user.
Can't find the answer to your doubts or questions?
Additionally, we offer training courses
Our flexible options of online training and face-to-face will provide you with all the knowledge necessary to understand and implement your software maintenance.